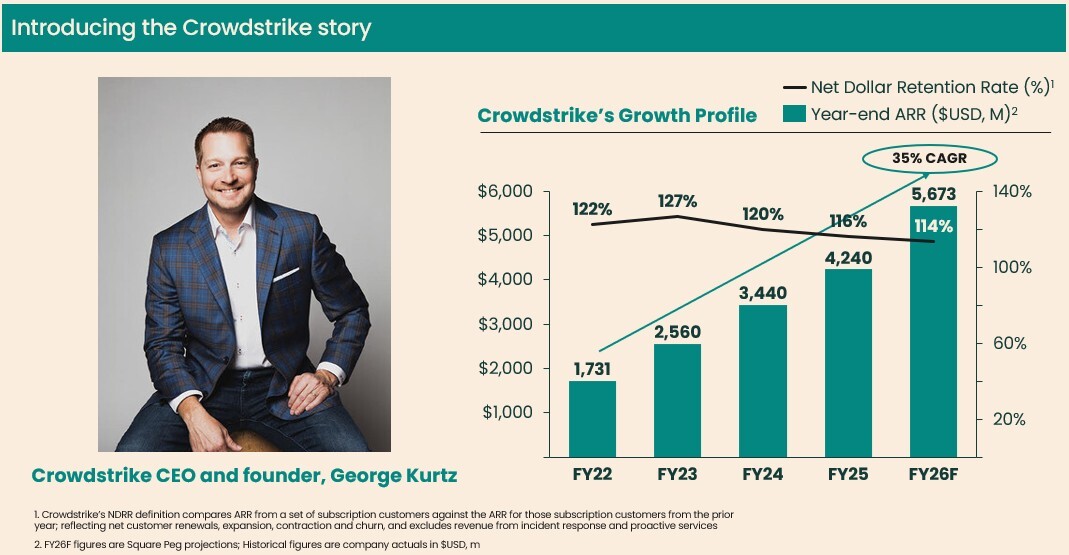
If you are reading this article from your corporate laptop or phone, there is a good chance that device is secured by Crowdstrike (NASDAQ: CRWD), the cybersecurity company founded by George Kurtz in 2011 that now protects the majority of the Fortune 500. However, if you are not in the cybersecurity industry, the first time you may have heard of the company was when a technical incident on July 19, 2024, caused ‘Blue Screens of Death’ to appear worldwide, requiring reboots of protected devices, from LaGuardia airport departure screens to suburban Melbourne ATMs.
This article takes a deeper dive into and presents the investment case for Crowdstrike. It will explain:
- Why we find the cybersecurity space attractive and how the evolution of the ‘threat cycle’ drives its dynamics;
- How Crowdstrike developed a leading product for endpoint protection;
- What our thesis is on the sustainability of Crowdstrike’s moat and its multiple levers of growth into adjacent markets; and
- How this founder-led business emerged stronger from the crucible of the July 19, 2024 incident
The Cybersecurity Market: How the ‘Threat Cycle’ Drives Its Dynamics
Enterprise cybersecurity has become one of the most dynamic and resilient sectors in the technology industry. Gartner forecasts 15%+ growth in cybersecurity spending in 2025 and a 12%+ p.a. growth rate over the next five years, while Chief Information and Security Officer (CISO) surveys consistently rank cybersecurity as a top-three priority for forward investment. This is for two reasons:
- First, the ‘threat cycle’. This concept references the continual “threat-response” dynamic that drives the industry. Typically, when adversaries innovate or ways of working change (e.g. the shift to cloud), new players in turn innovate on breakthrough solutions that can grow rapidly and become an industry standard (See Figure 1). That rapid adoption spurs competition from incumbents - often a race to acquire or develop that capability internally - or an opportunity for the new player to establish a moat and create significant value.
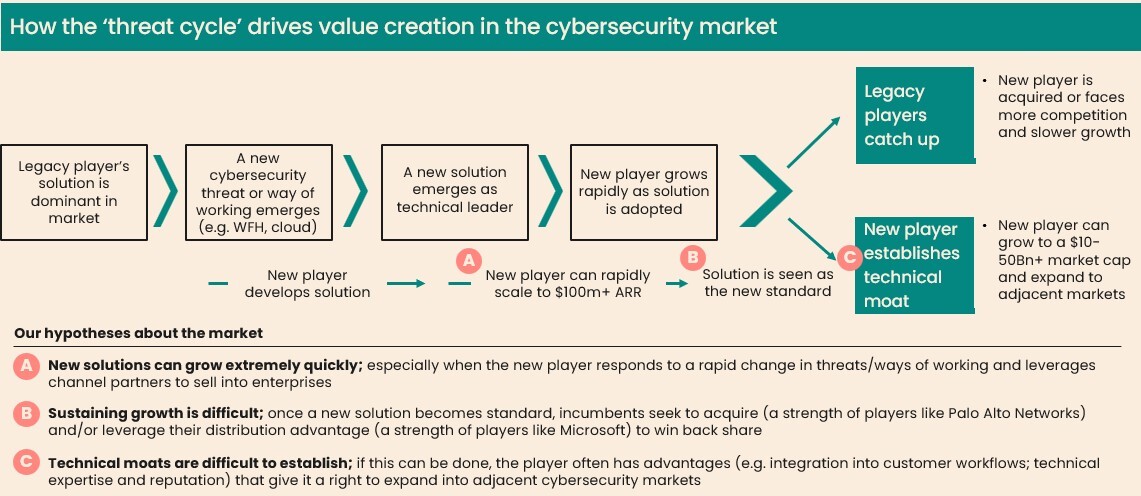
- Second, the proliferation of threat vectors (or what cyber assets need protecting) as the economy further digitises. This has led to vendors offering (often overlapping) protection across four key sub-markets:
(a) Endpoint Security: where platforms like Crowdstrike’s Falcon or Microsoft Defender protect end-user devices;
(b) Cloud Security: where players like **Wiz,** recently acquired by Alphabet, protect enterprise data, applications and infrastructure in the cloud;
(c) Network Security: where players like Palo Alto Networks and Cloudflare protect enterprise networks themselves from threats; and
(d) Identity and Access Management: where platforms like Okta authenticate users and determine who gets to access what.
In addition to these, there is a long tail of other sub-markets or ways of classifying the market, e.g. cloud security monitoring - and there is an increasingly blurred line between sub-markets as both threats and vendors cross vectors.
How Crowdstrike Built Its Lead in the Endpoint Security Market
An endpoint is any device that connects to a corporate network, such as laptops, tablets, wearables, IoT devices and PoS systems. Endpoints are proliferating, driven by the increasing affordability of devices and the growth of remote work (accelerated by COVID), with ~850 million new endpoints connected each year.
Most cybersecurity breaches begin at the endpoint, making it one of the most mission-critical sub-markets. Endpoint breaches can originate from anywhere, from sophisticated state-based hacker groups to phishing emails that catch you off guard with the promise of a gift card.
The evolution of endpoint protection is a case study of the threat cycle in action (see Figure 2). As malware developed in the 1990s, some may remember the era of installing McAfee Anti-Virus software directly onto desktop computers via floppy disk. In the early 2000s, as threats became more sophisticated, so did the protection offered by the next generation of players, such as Norton Anti-Virus. As work became increasingly distributed in the 2010s, real-time detection via ‘threat signatures’ and the fast response capabilities of Microsoft Defender became necessary to protect against increasingly live and adaptive threats, supported by regulatory requirements and industry standards.
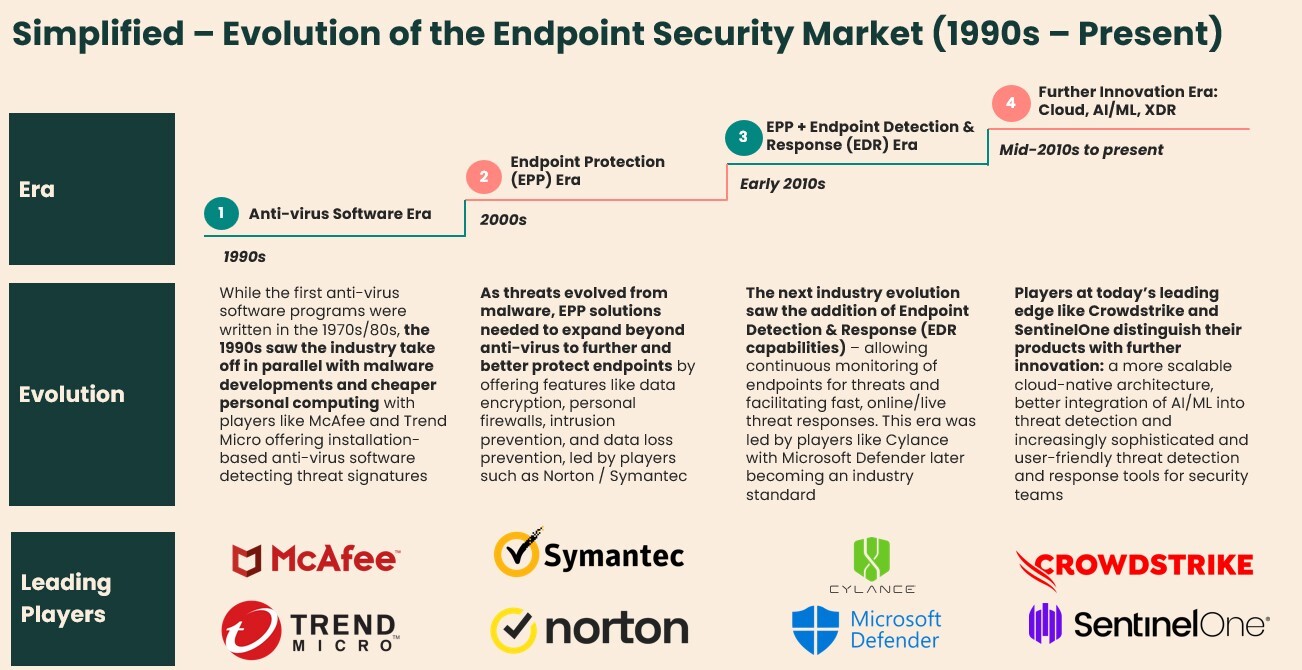
In the current era, Crowdstrike (and other cloud-native players) have uplifted endpoint protection via three main points of evolution:
- Cloud-native architecture: CrowdStrike operates on a cloud-native platform built on a highly scalable architecture, allowing it to process and analyse large amounts of data in real-time as well as deploy protection to devices in near real-time.
- ‘Crowdsourced protection’ powered by AI and ML models: Building on this cloud architecture, CrowdStrike harnesses the data from billions of endpoint events across the entire global community of protected devices. Coupled with sophisticated AI/ML models, this brings the threat cycle into near real-time: Crowdstrike’s platform can detect a threat signature on one device anywhere and move to protect all devices globally and near-instantly.
- Single pane of glass: Falcon has unified their endpoint protection offering with behavioural detection and 24/7 human threat hunters in the Falcon platform. This “single pane of glass” approach significantly simplifies security team operations and costs with convenient management and reporting through one cloud console.
But if these factors give Crowdstrike a leadership position today, what gives us confidence that this advantage has real durability going forward?
CISOs are responsible for ensuring their organisation continually benefits from the best available protection against breaches. We believe that Crowdstrike’s cloud-native approach brings the threat cycle to a new, real-time paradigm, where threat detection anywhere can lead to protection everywhere. In this paradigm, non-cloud native competitors will never be as effective, as these architectures will not have full access to or will be slower at handling a similar scale of information (>100s of billions of endpoint events per day) required to stay at the cutting edge of protection. Compared to cloud-native competitors like SentinelOne, Crowdstrike’s differentiation then becomes around how much data is harnessed by the platform and the continuing sophistication of AI/ML models supplemented by human cyber experts to remain at the frontier - which we believe show sustainability over at least the medium-term, supported by the network effect of Crowdstrike’s larger customer base, multi-product proliferation, and its investments into AI talent and R&D.
Another interlinked factor contributing to Crowdstrike’s success in the endpoint market is its partner-led go-to-market strategy, which helps displace legacy vendors. ~90%+ of Crowdstrike’s sales come via channel partners who are incentivised to sell Falcon to enterprises (which are often using legacy vendors) and leverage opportunities to sell such as following a cyber incident, during a cost review or at a point of contract renewal. An example of this is when Symantec’s enterprise business was sold to Broadcom and innovation slowed at the same time that Crowdstrike was building its reputation for real-time threat detection. Channel partners launched Symantec replacement campaigns en masse, bringing thousands of enterprises to Falcon. This partner-first strategy not only accelerated sales, but also created an ecosystem around Crowdstrike from platform-certified professionals and the popularity of its app store for third parties to make security products available.
Beyond Endpoint: Crowdstrike’s Multiple Levers of Growth
A core part of our investment thesis—and the critical ‘why now’ for those new to the company’s journey—is Crowdstrike’s evolution from a single-product endpoint security vendor into a broader cybersecurity platform, with the right to win in large, adjacent cybersecurity sub-markets and related products. We believe that this right-to-win is a function of three factors:
- First, its cloud architecture and single pane of glass make the addition and management of new modules more straightforward and their efficacy across the network or endpoints near-instant.
- The second is the virtuous cycle that the company’s endpoint reputation and channel partners have built, facilitating expansion beyond the core. Crowdstrike’s solutions are often seen as industry standard by the likes of Gartner, and channel partners have a clear sales and implementation playbook to follow. This has more recently been supplemented by Falcon Flex (a frictionless way to trial and scale up and down new products), which we will discuss further.
- The third is the muscle the organisation has built around smart build vs. buy decisions to bolster its adjacent capabilities, with several examples of Crowdstrike successfully ingesting a capability and acqui-hiring talent (e.g. Humio for log management) and quickly making the product feel like a seamless part of the platform (creating Falcon Logscale) vs. offering a clunky bolt-on.
Considered together, we believe the company has a clear path to reaching $10+Bn in ARR over the medium-term from both its organic and acquired adjacent offerings that are now outpacing the core endpoint product in growth. These ‘breakout’ offerings are:
- Identity and Access Management: At the end of FY25, this offering represented $600m in ARR, 14% of total, growing >45% year-on-year. This offering began with the acquisition of Preempt for their capabilities in stopping identity-based attacks and has now extended into a broader access management offering, leveraging Crowdstrike’s advantages of endpoint connectivity and the single pane of glass for management
- Cloud Security: At the end of FY25, this offering represented $370m in ARR, 14% of total, growing >20% year-on-year The key motion here has been displacing ‘point’ cloud solutions in favour of clients who would rather Crowdstrike as a best-of-suite vendor across their security needs
- Next-Gen SIEM: At the end of FY25, this represented $330m in ARR, 8% of total, growing >115% year-on-year. The growth story here is primarily about displacing legacy log/SIEM providers with Falcon’s logscale product offering a large jump in speed and scalability
- New Products: The company has several products on the horizon, all of which are evolving with similar growth potential, notably in the areas of autonomous SOC and vulnerability management
In addition to these growth vectors, Crowdstrike has a strong financial model with impressive growth, retention and margin metrics, including:
- Annual Recurring Revenue of $4.4Bn in Q1FY26, growing 22% year-on-year
- Net Retention of 112% and Gross Retention of 97% at end FY25
- Subscription Gross Margin of 77% in Q1FY26
- Free Cash Flow Margin of 25% in Q1FY26
Founder Under Fire: George Kurtz and the 2024 Outage
Kurtz demonstrates many of the attributes that Square Peg looks for in its best founders. He brings to bear not just deep product and domain expertise (as an executive at McAfee, he literally “wrote the book” on cybersecurity in the 1990s), but a clear vision of becoming the “Security Cloud,” akin to what Salesforce is for CRM.
In building our conviction about Kurtz as a founder, we also noted his zeal for sales and the customer, which has been reflected in the organisation’s DNA, orienting decision-making in every department around customer needs. In addition, the company has become a ‘talent magnet’, partly because of its reputation for being at the industry’s cutting edge, fostering a culture of performance, top-of-market incentives, and talent flows from competitors and leading tech sales organisations.
Kurtz and the team faced their most notable recent test on July 19, 2024. The company distributed a faulty update to its Falcon Sensor software, resulting in widespread issues with Microsoft Windows computers that were running the software. This incident resulted in 8.5 million systems requiring manual reboot and media notoriety for one of history’s largest and most costly IT outages. While the incident is regrettable, Kurtz and his team’s response in the months following has helped build our conviction further. Beyond taking responsibility and working hand-in-hand with clients, Kurtz told attendees at the 2024 Fal.Con conferences to ‘never let a good crisis go to waste’. The company offered customer care packages that included free credits to encourage the adoption of a new innovation in the company’s model, Falcon Flex. Falcon Flex allows customers to commit to a specific level of spend and enjoy frictionless access to the entire CrowdStrike portfolio of modules, facilitating easier experimentation across the product suite and scalability. In Q1 FY26, Crowdstrike reported that accounts that had adopted Falcon Flex soared to $3.2 billion in total deal value, growing >120% year-on-year.
Conclusion: Sources of Sustainable Advantage in Cybersecurity
One of the takeaways from CrowdStrike’s story is an understanding of how exceptional it is to create enduring value in the cybersecurity market. In the industry’s dynamic of the ‘threat cycle’ - where adversaries can develop new threats quickly and the next generation of breakthrough solutions can rapidly grow - many of these breakthrough solutions will either be acquired or face stiff competition if they cannot develop a meaningful moat.
In the case of Crowdstrike, a cloud-first architecture decision that brings in data from an entire global network of protected devices, combined with the continual refinement of AI and ML models over the past decade, has created an enduring source of advantage in endpoint security. Kurtz has built an organisation with the DNA required to build from its initial sources of advantage to win in large new markets amidst a shifting landscape. We look forward to following Crowdstrike on their growth journey and sharing more updates on the business in the future.
Want to learn more about Square Peg's Global Tech Fund or explore investing?
Read more about our strategy to back founder-led businesses in the public markets, as well as our investment philosophy. Click here to contact Square Peg Investor Relations.

.svg)


